Our research seeks to empower individuals and organizations to control
how their data is used. We use techniques from cryptography,
programming languages, machine learning, operating systems, and other
areas to both understand and improve the security of computing as
practiced today, and as envisioned in the future.
 Security Research Group Lunch (12 December 2017)
Security Research Group Lunch (12 December 2017)
Haina Li,
Felix Park,
Mainuddin
Jonas,
Anant Kharkar,
Faysal Hossain Shezan,
Fnu Suya,
David Evans,
Yuan Tian,
Riley Spahn,
Weilin Xu,
Guy "Jack" Verrier
Everyone is welcome at our research group meetings. To get
announcements, join our Slack
Group (any @virginia.edu email address can join themsleves,
or email me to request an invitation).
Projects
News
21 April 2011
Our paper,
Faster Secure Two-Party Computation Using Garbled Circuits by Yan Huang, David Evans, Jonathan Katz, Lior Malka.
was accepted to USENIX Security. Yan will present the paper at the conference in San Francisco in August. If you would like an advance copy, email me and I will let you know when it is available.
Posted in Papers, Secure Computation | Comments Off
4 April 2011
Congratulations to Yan Huang for winning an Honorable Mention at the University of Virginia Engineering Research Symposium (UVERS) for his poster on privacy-preserving biometric matching.
The poster is here: [PDF (13MB)]
Posted in Awards, Privacy, Research | Comments Off
28 March 2011

Jonathan Burket, Patrick Mutchler, Michael Weaver, and Muzzammil Zaveri will present GuardRails: A (Nearly) Painless Solution to Insecure Web Applications at the RubyNation conference in Reston (near Washington, DC), on April 2.
With web applications continuing to grow in popularity and frameworks becoming simpler to use, creating a web application is easier than ever. While building an application may be straightforward, ensuring that it is secure requires both a deep understanding of subtle security vulnerabilities as well as tedious and careful insertion of security checks. We propose GuardRails, an open source source-to-source tool for Ruby on Rails applications that adds extra layers of security to web applications with only minimal effort from the developer. GuardRails works by attaching security policies to the data itself. These policies are automatically enforced throughout the application, without the need for the developer to write large amounts of code. Our system helps prevent against a variety of security vulnerabilities from CrossSite Scripting to faulty access controls without requiring the developer to have a sophisticated knowledge of web security.
Posted in Conferences, Research, Security | Comments Off
4 February 2011
Our paper on using lattice ciphers for low-power public-key encryption targeted to RFID tags is now available. Yu Yao will present the paper in Wuxi, China in April.
Yu Yao, Jiawei Huang, Sudhanshu Khanna, abhi shelat, Benton Highsmith Calhoun, John Lach, and David Evans. A Sub-0.5V Lattice-Based Public-Key Encryption Scheme for RFID Platforms in 130nm CMOS. 2011 Workshop on RFID Security (RFIDsec’11 Asia)
Wuxi, China. 6-8 April 2011.
Abstract: Implementing public-key cryptography on passive RFID tags is very challenging due to the limited die size and power available. Typical public-key algorithms require complex logical components such as modular exponentiation in RSA. We demonstrate the feasibility of implementing public-key encryption on low-power, low cost passive RFID tags to large-scale private identification. We use Oded Regev’s Learning-With-Error (LWE) cryptosystem, which is provably secure under the hardness assumption of classic lattice problems. The advantage of using the LWE cryptosystem is its intrinsic computational simplicity (the main operation is modular addition). We leverage the low speed of RFID application by using circuit design with supply voltage close to transistor threshold (Vt) to lower power. This paper presents protocols for using the LWE cipher to provide private identification, evaluates a design for implementing those protocols on passive RFID tags, and reports on simulation experiments that demonstrate the feasibility of this approach.
Full paper (19 pages): [PDF]
Posted in Conferences, Papers, Privacy, Research, RFID, Security | Comments Off
24 December 2010
Karsten Nohl is in the news again, this time for demonstrating how bad the proprietary crypto used for car immobilizers is. Here are a few articles:
Karsten presented the technical aspects in a talk at the 8th Embedded Security in Cars conference in Berlin.
Even if car manufacturers get the crypto right, relay attacks pose a serious threat, especially for modern cars that do away with the mechanical key completely. See the upcoming NDSS paper by Aurelien Francillon, Boris Danev, and Srdjan Capkun: Relay Attacks on Passive Keyless Entry and Start Systems in Modern Cars.
Posted in Cryptography, Research, RFID, Security | Comments Off
9 December 2010
We’ve released our code and paper on efficient privacy-preserving biometric identification:
Yan Huang (University of Virginia), Lior Malka (Intel/University of Maryland), David Evans (University of Virginia), and Jonathan Katz (University of Maryland). Efficient Privacy-Preserving Biometric Identification. To appear in 18th Network and Distributed System Security Conference (NDSS 2011), 6-9 February 2011. [PDF, 14 pages]
We present an efficient matching protocol that can be used in many privacy-preserving biometric identification systems in the semi-honest setting. Our most general technical contribution is a new backtracking protocol that uses the by-product of evaluating a garbled circuit to enable efficient oblivious information retrieval. We also present a more efficient protocol for computing the Euclidean distances of vectors, and optimized circuits for finding the closest match between a point held by one party and a set of points held by another. We evaluate our protocols by implementing a practical privacy-preserving fingerprint matching system.
Yan will present the paper at NDSS in February. The code for our system is available under the MIT open source license.

flickr cc: didbygraham
Posted in Conferences, Papers, Privacy, Research, Security | Comments Off
9 November 2010
Jonathan Burket, Patrick Mutchler, Michael Weaver and Muzzammil Zaveri will present GuardRails at AppSec DC on Wednesday, 10 November. The conference is at the Walter E. Washington Convention Center in Washington, DC.
GuardRails is a framework for automating many of the tasks necessary to build a security web application. For more, see the talk abstract: GuardRails: A Nearly Painless Solution to Insecure Web Applications. (and video and slides will appear there soon)
Update 9 December: The slides are here [PDF].
Posted in Conferences, Program Analysis, Research, Security, Software Engineering | Comments Off
7 September 2010
I’m a judge for the Deutsche Post “Security Cup” contest being organized by our former student, Karsten Nohl. The goal of the contest is to incentivize enterprising students and practitioners to bash on the Deutsche Post’s E-Postbrief web application. They are offering some fairly significant prizes (up to 5,000 Euro per bug) to teams that identify vulnerabilities in their application, as well as providing up-front funding to qualified teams that enter the contest.
Deutsche Post Page
EPostal News
Posted in Contests, Security | Comments Off
3 May 2010
Yuchen Zhou will present a paper [PDF] on HTTP-only cookies and why it is so hard to deploy security technologies at Web 2.0 Security and Privacy (attached to the Oakland conference) on May 20.
HTTP-only cookies were introduced eight years ago as a simple way to prevent cookie-stealing through cross-site scripting attacks. Adopting HTTP-only cookies seems to be an easy task with no significant costs or drawbacks, but many major websites still do not use HTTP-only cookies. This paper reports on a survey of HTTP-only cookie use in popular websites, and considers reasons why HTTP-only cookies are not yet more widely deployed.
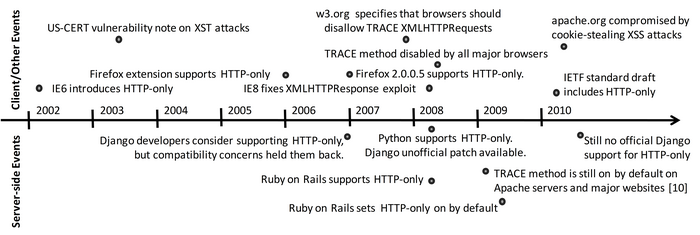
Posted in Conferences, History, Papers, Security | Comments Off
19 April 2010
Nate Paul, who finished a PhD in our group a few years ago and is now a research scientist at Oak Ridge National Labs, is the focus of this CNN story: Scientists work to keep hackers out of implanted medical devices, CNN, 16 April 2010.
Nathanael Paul likes the convenience of the insulin pump that regulates his diabetes. It communicates with other gadgets wirelessly and adjusts his blood sugar levels automatically.
But, a few years ago, the computer scientist started to worry about the security of this setup.
What if someone hacked into that system and sent his blood sugar levels plummeting? Or skyrocketing? Those scenarios could be fatal.
“If your computer fails, no one dies,” he said in a phone interview. “If your insulin pump fails, you have problems.”
As sci-fi as it sounds, Paul’s fears are founded in reality.
…
Posted in Cryptography, Medical Devices, Security | Comments Off




