Explicating SDKs
27 June 2013Security exploits nearly always stem from attackers finding ways to violate assumptions system implementers relied upon. As a simple example, consider a classic buffer overflow attack which is possible because the implementers assumed (perhaps implicitly) that the size of some data could not exceed the buffer size, but an attacker found a way to create an input that violates that assumption.
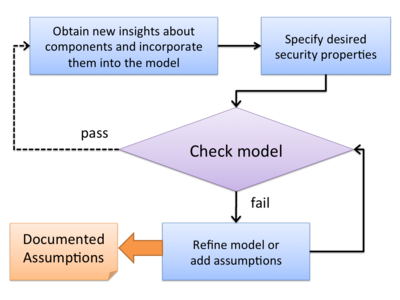
In this work, joint with colleagues at Microsoft Research, we consider the implicit assumptions upon which secure use of single sign-on SDKs depends. Our study of three important authentication and authorization SDKs (including Facebook’s) supports the need for systematically explicating SDKs to uncover these assumptions. We found assumptions that were critical to secure use of the SDKs, but that were not clearly documented and were subtle enough to be missed by the majority of tested apps.
We advocate that a systematic explication process for uncovering these assumptions should be part of the engineering process for developing security-critical SDKs.
For details, see our paper:
