Our paper on side-channel analysis of web applications is now available:
Peter Chapman and David Evans. Automated Black-Box Detection of Side-Channel Vulnerabilities in Web Applications. In 18th ACM Conference on Computer and Communications Security (CCS 2011), Chicago, IL. 17-21 October 2011. [PDF, 12 pages]
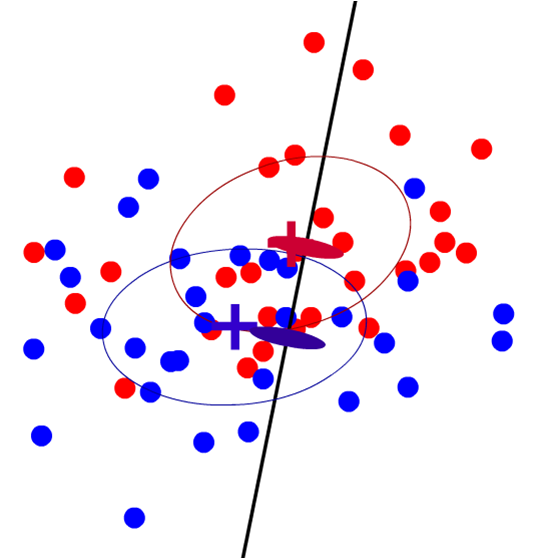
The paper describes a black-box tool for detecting side-channel vulnerabilities by analyzing network traffic over repeated crawls of a web application. Our tool quantifies the severity of side-channel leaks in a web application, and gives web application developers a measure of the risk of information leakage against different types of adversaries. The frequent and highly dynamic client-server communication that is characteristic of modern web applications leaves them vulnerable to side-channel leaks where an adversary can learn about the state of the application and visitor’s choices, even over encrypted connections. Our approach provides a new way to quantify the severity of these vulnerabilities based on analyzing the results of traces of the web traffic using the Fisher criterion.

Peter will present the paper at CCS in Chicago in October.
Project Site