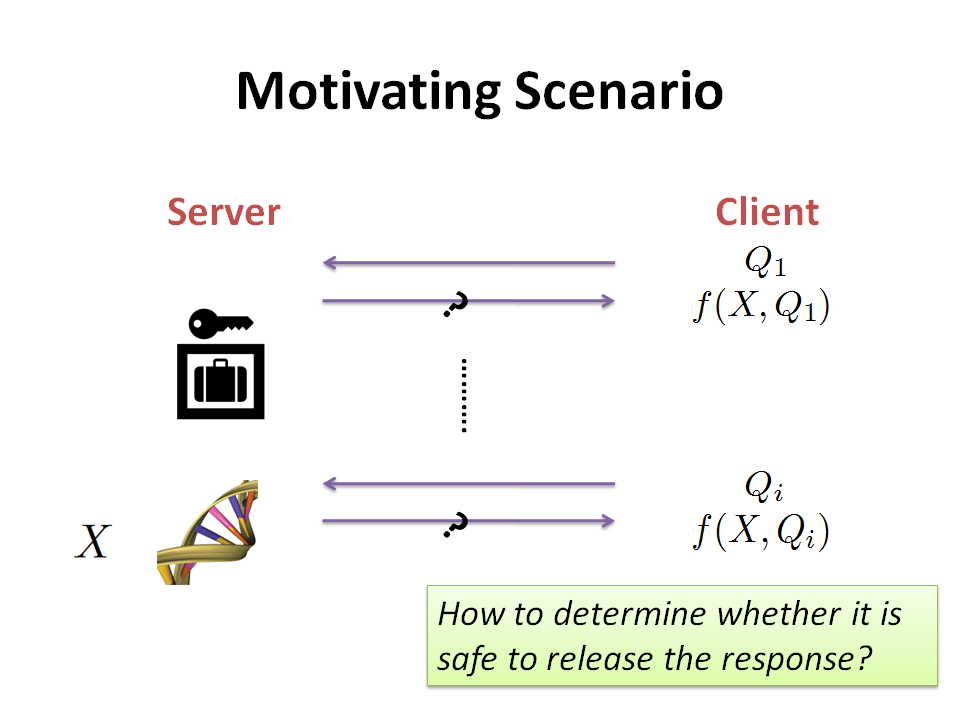
Our research seeks to empower individuals and organizations to control
how their data is used. We use techniques from cryptography,
programming languages, machine learning, operating systems, and other
areas to both understand and improve the security of computing as
practiced today, and as envisioned in the future.
 Security Research Group Lunch (12 December 2017)
Security Research Group Lunch (12 December 2017)
Haina Li,
Felix Park,
Mainuddin
Jonas,
Anant Kharkar,
Faysal Hossain Shezan,
Fnu Suya,
David Evans,
Yuan Tian,
Riley Spahn,
Weilin Xu,
Guy "Jack" Verrier
Everyone is welcome at our research group meetings. To get
announcements, join our Slack
Group (any @virginia.edu email address can join themsleves,
or email me to request an invitation).
Projects
News
14 October 2011
UVa Today has a story about our secure computation project: U.Va. Team Awarded $3 Million NSF Secure Computation Grant, Fariss Samarrai, UVa Today, 14 October 2011.
Photo: Cole Geddy
“Secure computation is the idea that you can have two people compute a function that depends on things that each one knows individually and wants to keep private without exposing their private data to the other person, or to anyone else,” Evans said.
The research has applications in everyday life, from private medical information, such as personal genomics, to privacy-preserving face recognition and electronic commerce.
As a simple example of how it works, consider two people who each have smartphones with personal address books. They would like to know if they know any of the same people by comparing their address books. But, they may not want to share their address books, which include potentially sensitive private information. So how can they find the common entries, without revealing anything about their other contacts?
Read More …
Posted in News, Privacy, Research, Secure Computation, Smartphones | Comments Off
11 October 2011
Posted in Conferences, Research, Secure Computation, Talks | Comments Off
21 September 2011
Here are the slides from my talk in cs6190, our seminar for new graduate students: [PPTX] [PDF]
Links from the talk:
Posted in Research, Secure Computation, Talks | Comments Off
20 September 2011

Computers will make the world of tomorrow a much safer place. They will do away with cash, so that you need no longer fear being attacked for your money. In addition, you need not worry that your home will be burgled or your car stolen. The computers in your home and car will guard them, allowing only yourself to enter or someone with your permission.
However, there is one kind of crime which may exist in the future — computer crime.
From World of Tomorrow — School, Work and Play, by Neil Ardley, 1981. (Scanned by David Gagnon. Hat tip: Ian Finder, University of Washington)
Posted in History, News | Comments Off
14 September 2011
Yuchen Zhou presented Protecting Private Web Content from Embedded Scripts at ESORICS in Belgium.
His talk slides are here: [PPTX] [PDF]
Posted in Talks, Web Security | Comments Off
30 August 2011

Today (August 30th) we are hosting the Kickoff Meeting for our new NSF-funded 5-year project, Practical Secure Two-Party Computation: Techniques, Tools, and Applications. This is a collaborative research project with abhi shelat and Aaron Mackey at UVa, Michael Hicks and Jonathan Katz at the University of Maryland, and Steven Myers at Indiana University. The goal of the project is to make privacy-preserving computation practical and accessible enough to be used routinely in applications such as personalized genetics, medical research, and privacy-preserving biometrics. For more, see //securecomputation.org.
Posted in Research, Secure Computation | Comments Off
30 August 2011
The Computer Science department has moved into Rice Hall, our beautiful new building next to our former home in Olsson Hall.
Here are some pictures of the lab space for the Secure Research Group in Rice 442:

Meeting space in lab room (yes, the big curved white wall in the back is a whiteboard!)



Samee Zahur checking the lights

Plenty of room to grow!

But, it may be a bit of a wait for that bagel!

View from my office
Posted in Pictures, Research | Comments Off
30 August 2011
Yikan Chen and I are releasing a paper today on Auditing Information Leakage for Distance Metrics. The paper is a first step towards the goal of developing self-auditing secure computations that can determine when the output of a secure computation would leak too much information to be safe to release. Yikan will present the paper at the Third IEEE Conference on Privacy, Security, Risk and Trust in Boston, 9-11 October 2011.
Abstract. Many useful scenarios involve allowing untrusted users to run queries against secret data, so long as the results do not leak too much information. This problem has been studied widely for statistical queries, but not for queries with more direct semantics. In this paper, we consider the problem of auditing queries where the result is a distance metric between the query input and some secret data. We develop an efficient technique for estimating a lower bound on the entropy remaining after a series of query-responses that applies to a class of distance functions including Hamming distance. We also present a technique for ensuring that no individual bits of the secret sequence is leaked. In this paper, we formalize the information leakage problem, describe our design for a query auditor, and report on experiments showing the feasibility and effectiveness of our approach for sensitive sequences up to thousands of bits.
Full paper: [PDF, 10 pages]
Posted in Papers, Research, Secure Computation | Comments Off
23 August 2011

Muzzammil Zaveri (BACS 2011), who worked in our group 2010-2011, and Ethan Fast (BACS 2011) have launched a new company, Proxino, that provides developers with a way of finding bugs in their site’s JavaScript code, as well as optimizing the loading and performance of scripts. Ethan and Muzzammil were funded by Y Combinator, starting in Summer 2011 (right after finishing their BACS degrees). Here’s an article about Proxino:
YC-Funded Proxino: Automated Error Reporting For Your Client-Side JavaScript, TechCrunch, 22 August 2011.
While he was a student here, Muzzammil worked on the GuardRails secure web application framework. Ethan worked in Westley Weimer‘s group on automated program repair.
Posted in News | Comments Off
21 August 2011
Videos from all the talks at USENIX Security are now available on the conference site.
Here are the talks by UVa people:
I would also highly recommend Collin Jackson’s invited talk on Crossing the Chasm: Pitching Security Research to Mainstream Browser Vendors.
Posted in Conferences, Security, Talks | Comments Off